Threat Intelligence and Incident Response in Industrial and Robotics environments
 18 February,2023 - BY admin
18 February,2023 - BY admin
Threat Intelligence and Incident Response in Industrial and Robotics environments
The emergence of Digital Twins (DT) in industry has been a major breakthrough in the improvement of industrial processes. It has also allowed the inclusion of simulations in an environment where trial-and-error method was used up to now, thus minimising the industrial waste generated by these tests and optimising the industrial process by means of different data processing techniques.
The use of meta-operating system frameworks such as Robot Operating System (ROS) provides multiple possibilities to interact with the robot and optimise its operation in real time. Nevertheless, the libraries and the protocols they use (ROSTCP and ROSUDP) have security vulnerabilities (e.g. ROS v1 was not designed with security considerations) that can provoke an external attacker to gain control of the robot. This may lead to consequences at shopfloor level, such as damaging the system, stopping production, or even affecting the safety of an operator.
To avoid such problems, well-planned Incident Response (IR) and Threat Intelligence (TI) services enable an organisation to identify potential security issues and react to them before they cause further damage.
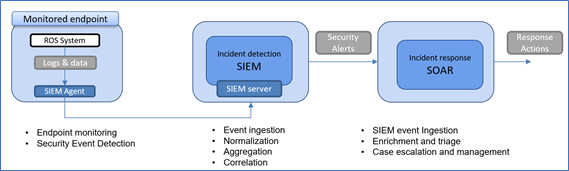
In the context of the ODIN project, based on MaGMa Use Case and MITRE ATT&CK Frameworks, a cyber kill chain for robotic production systems has been modelled. A cybersecurity detection and response system (see Figure 1) has also been developed to mitigate the detected attacks and minimise the damage on the robotics environment.
img1
A Cyber Kill Chain is a successful sequence of actions to gain access to a target by using different attack tactics and techniques from the MITTRE ATT&CK model. In ODIN, a cyber kill chain has been defined to detect ROS communications on the network and replicate the actions of the ROS master from the attacking host to the robot environment. The steps are as follow:
- Reconnaissance stage: The first step is to discover the network. This can be done with SoTA tools such as Nmap, to identify the hosts present in the network and their open ports, and to detect in this case the host from which the ROS communication is taking place.
- Privilege Scalation stage: Once the target is identified, a ROS scan is performed, through the SoTA tool ROSPenTo, to discover the different nodes and topics of the ROS ecosystem.
- Cyber Intrusion stage: Using this information, ROSPenTo is able then to disconnect nodes from the ROS network and even send fake malicious requests to the ROS client installed on the robot.
The responsibility of the cybersecurity providers is to be aware of the possible cyber kill chains affecting the system, and to be prepared to detect and mitigate the attacks as soon as they occur. For this, there are tools such as SIEM (Security Event and Information Management) with the capabilities of collection of logs and data from the network and systems and generate the corresponding security events; and SOAR (Security Orchestration, Automation and Response) with the capabilities of defining automation workflows that guide the incident response actions.
By combining threat intelligence with SIEM and SOAR platforms, incident responders can, on the one hand enrich their log file indicators and prioritise alerts, and on the other hand use indicators of risk to execute automated attack mitigations and improve the effectiveness of incident response.
For more information about cybersecurity and Threat Intelligence in Industrial and Robotics environments, see the following references:
- Hearn, M., & Rix, S. (2019). Cybersecurity considerations for digital twin implementations. IIC J. Innov, 107-113.
- Zhu, Q., Rass, S., Dieber, B., & Vilches, V. M. (2021). Cybersecurity in robotics: Challenges, quantitative modeling, and practice. Foundations and Trends® in Robotics, 9(1), 1-129.
- Incident Response & Threat Intelligence – Guidepoint Security: https://www.guidepointsecurity.com/incident-response-and-threat-intelligence/
Get the latest news on ODIN right to your inbox!
Newsletter Permission: The ODIN project will use the information you provide in this form to be in touch with you and to provide updates and news. Please let us know if you would like to hear from us:
ODIN newsletter: You can change your mind at any time by contacting us at info@odinh2020.eu. We will not distribute your email address to any party at any time.

Comments (0)